Fuzzing TCPdump to find CVE-2017-13028
Fuzzing with AFL++ is a great way to find complex vulnerabilities. I'm pretty new to fuzzing binaries, so based on the amazing repo Fuzzing101, I've recreated the finding of CVE-2017-13028 in TCPdump.
The goal is to find a crash/PoC for CVE-2017-13028 in TCPdump 4.9.2.
Objectives:
- Finding an efficient way to fuzz TCPdump -
-vvvvXX -ee -nn -rand parallel fuzzing. - Enabling ASan for fuzzing -
AFL_USE_ASAN=1to find memory leaks and crashes. - Triage the crashes to find a PoC for the vulnerability
To read a file in tcpdump we can use the -vvvvXX -ee -nn -r flags to read from a file.
tcpdump -vvvvXX -ee -nn -r test.pcap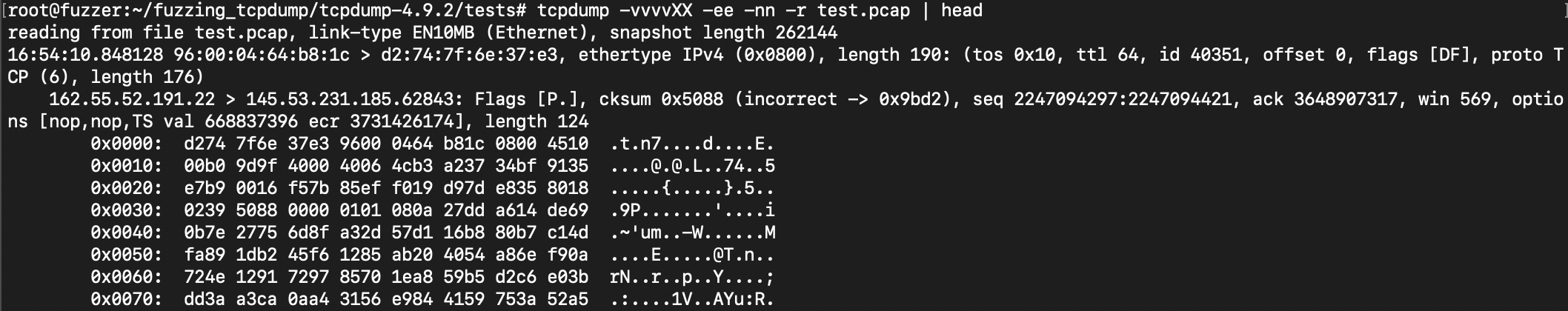
When fuzzing network protocols or applications, these flags provide maximum visibility into the malformed packets being generated and the target's responses, allowing you to see exactly what payload triggered unexpected behavior.
The hex dump (-XX) and maximum verbosity (-vvvv) are especially critical for identifying which specific bytes or protocol fields in the fuzzed packets caused crashes or vulnerabilities in the target system.
First download and unpack tcpdump 4.9.2 and validate that it works
https://www.tcpdump.org/release/tcpdump-4.9.2.tar.gz && tar -xvzf tcpdump-4.9.2.tar.gz && wget https://www.tcpdump.org/release/libpcap-1.8.0.tar.gz && tar -xvzf libpcap-1.8.0.tar.gz
Compile the libpcap with ASan
CC=afl-clang-lto ./configure --enable-shared=no --prefix="$HOME/fuzzing_tcpdump/install/" && AFL_USE_ASAN=1 make
Compile tcpdump with ASan
Compiling tcpdump, was not working until I saw this thread: on github-issues-97
CFLAGS="-Wno-error=implicit-function-declaration -Wno-error=implicit-int -fsanitize=address" AFL_USE_ASAN=1 CC=afl-clang-lto CXX=afl-clang-lto++ \
./configure --enable-shared=no --prefix="$HOME/fuzzing_tcpdump/install/" && AFL_USE_ASAN=1 make && AFL_USE_ASAN=1 make install
Confirm everything is working
$HOME/fuzzing_tcpdump/install/sbin/tcpdump --version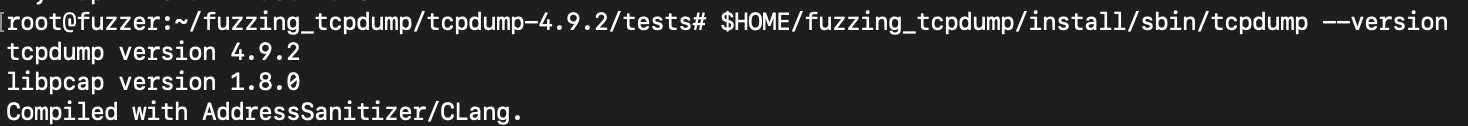
Running AFL++ in parallel to increase speed
For maximum efficiency, deploy AFL++ in parallel mode across multiple CPU cores:
afl-fuzz -i $HOME/fuzzing_tcpdump/tcpdump-4.9.2/tests/ \
-o $HOME/fuzzing_tcpdump/out/ \
-M fuzzer01 \
-s 123 \
-m none \
-- $HOME/fuzzing_tcpdump/install/sbin/tcpdump -vvvvXX -ee -nn -r @@Then instead of running the master thread, we run the slave thread. which we can do by adding the -S flag.
Starting with for example, fuzzer02, fuzzer03, fuzzer04, etc.
afl-fuzz -i $HOME/fuzzing_tcpdump/tcpdump-4.9.2/tests/ \
-o $HOME/fuzzing_tcpdump/out/ \
-S fuzzer02 \
-s 123 \
-m none \
-- $HOME/fuzzing_tcpdump/install/sbin/tcpdump -vvvvXX -ee -nn -r @@Note: ASAN on 64-bit systems requests a lot of virtual memory.
That's why I've set the flag "-m none" that disable memory limits in AFL
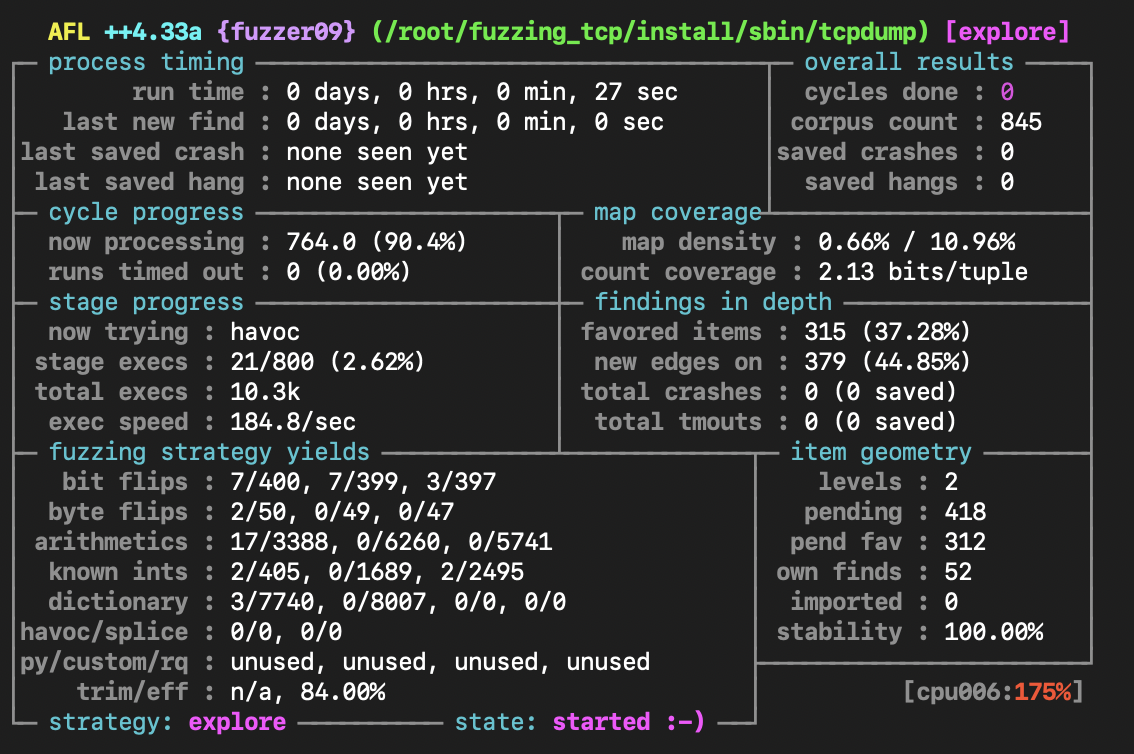
Let this continue for a while and check the status after a while with
afl-whatsup -s $HOME/fuzzing_tcpdump/out/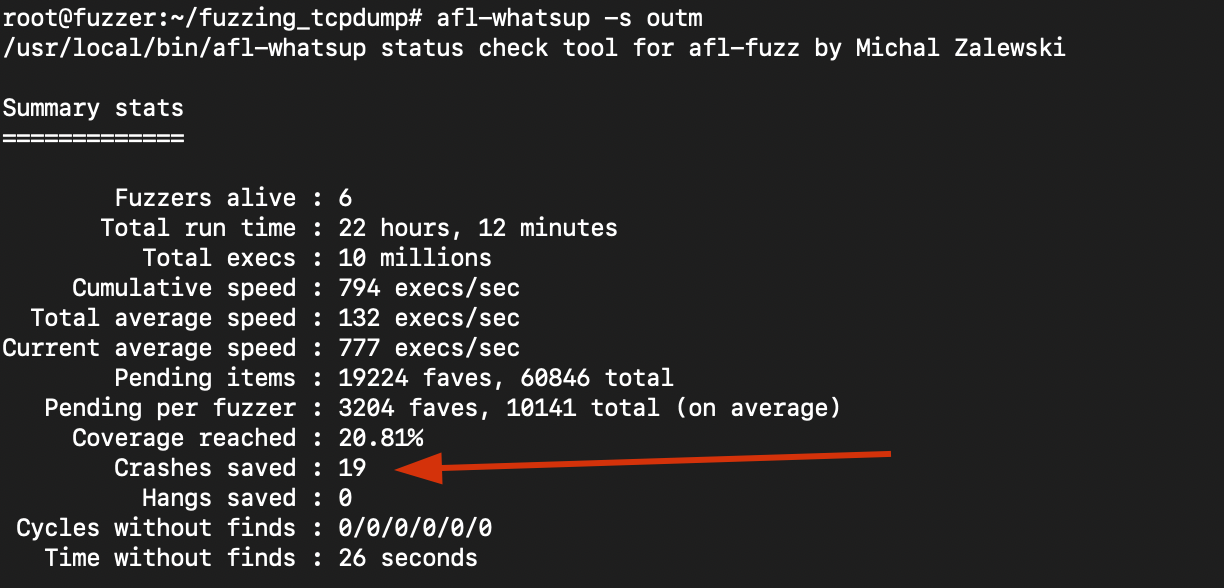
Here we see that we’ve already found 19 crashes of particulair input when fed to tcpdump. Next up is to triage the crashes to make a PoC for the vulnerability.