SSL pinning is a critical security mechanism in Android applications that helps prevent man-in-the-middle (MITM) attacks by validating server certificates against a predefined set of trusted certificates embedded within the application. While this security measure is essential for production applications, security researchers and developers often need to bypass it for legitimate testing purposes. This guide will walk you through the complete process of setting up an environment to bypass SSL pinning on Android, using a combination of powerful tools and techniques.
Download Android Studio
- And open
Virtual Device Manager - Choose an device without PlayStore and With a lower api than the newest one. In my case I went for
Pixel 5WithAPI 31
Setup ADB
- This is to get shell access to the Android phone after it's started
Setup RootAVD
git clone https://gitlab.com/newbit/rootAVD.git
cd rootAVD
./rootAVD.sh ListAllAVDs
./rootAVD.sh system-images/android-31/google_apis/x86_64/ramdisk.img #Could be different in your caseStart With Write-System
- To be able to copy files etc
emulator -avd Pixel_5_API_31 -writable-systemadb root
adb remount
adb shellExport the cert.der in Burpsuite and push it
openssl x509 -inform DER -in cacert.der -out cacert.pem
openssl x509 -inform PEM -subject_hash_old -in cacert.pem | head -1
OUTPUT : 9a5ba575
mv cacert.pem 9a5ba575.0
adb push 9a5ba575.0 /sdcard/
adb shell
su
mount -o rw,remount /system
cp /sdcard/9a5ba575.0 /system/etc/security/cacerts/
chmod 644 /system/etc/security/cacerts/9a5ba575.0
rebootDownload Frida and push and run it
xz -d frida-server-16.6.6-android-x86_64.xz
mv frida-server-16.6.6-android-x86_64 frida-server
adb push frida-server /data/local/tmp
adb shell "chmod 755 /data/local/tmp/frida-server"
adb shell "/data/local/tmp/frida-server &"Install the APK to the emulator
adb install nl.ian.apkObjection to start SSL pinning bypass
# Start Objection
objection -g your.package.name explore
# Disable SSL pinning
android sslpinning disable
# Verify bypass
android hooking list classes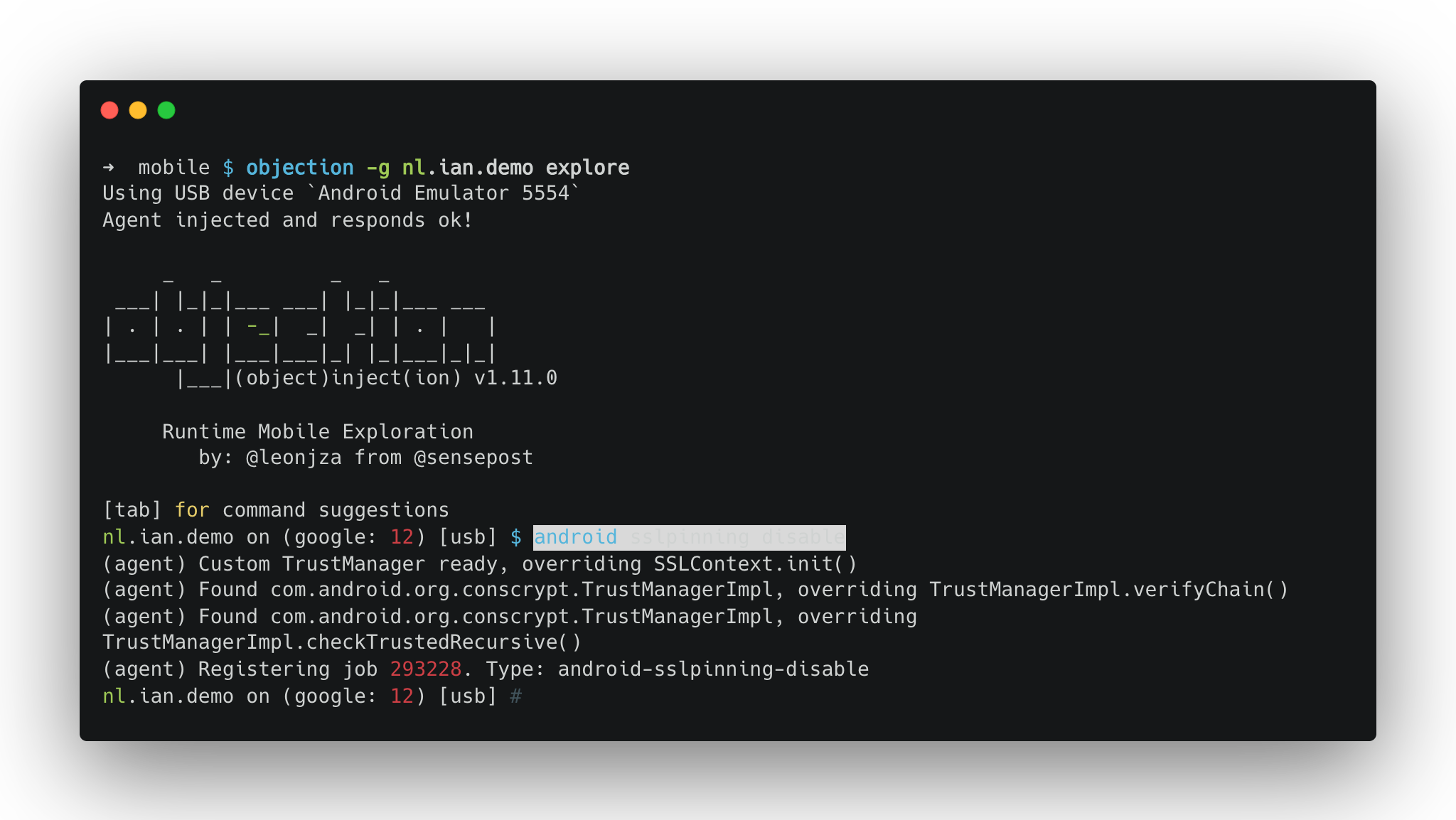
Dont forget to listen in burpsuite on all interfaces and configure the proxy in the emulator device.